Articles and write ups in the industry about Duty of Care Risk Analysis (DoCRA)
DoCRA Cited as Risk Assessment Methods to Demonstrate Reasonableness
STATE OF OHIO OFFICE OF THE ATTORNEY GENERAL IN THE MATTER OF DNA DIAGNOSTICS CENTER, INC. p. 7
COMMONWEALTH OF PENNSYLVANIA v. HERFF JONES, p. 5
ATTORNEY GENERAL OF THE STATE OF NEW YORK and HERFF JONES, p. 5
DoCRA Cited in Industry Publications
Podcast: Due Diligence as a Risk Management Approach
“Can you “demonstrate due diligence to a defensible standard of care” as your risk management approach? This would replace “”red/yellow/green”” approaches or advanced statistics. Let’s find out with our guest, Karen Worstell, who is a “Senior Cybersecurity Strategist” and a “CxO Security Advisor” with VMware. Your hosts are Kip Boyle, CISO with Cyber Risk Opportunities, and Jake Bernstein, Partner with K&L Gates.
DoCRA is included in the discussion.
DoCRA Cited in Industry Publications
As regulations and privacy laws require ‘reasonable security’, more organizations are focusing on their duty of care regarding decisions on risk and cybersecurity. More references to ‘reasonableness’ are being cited in breach litigation and security programs. An organization’s ideal goal is to have all relevant teams involved in analyzing the appropriate risk for their unique business environment. It is a positive sign that there are increased efforts to incorporate all perspectives to mitigate risk and manage cyber threats – and finding a common language to do so. And more importantly, developing a security program holistically.
The Duty of Care Risk Analysis (DoCRA) standard provides guidance in implementing reasonable security. CIS RAM is based upon the DoCRA standard. Other experts have referenced DoCRA and CIS RAM in their cybersecurity and risk publications. A few titles are featured below.
CISO COMPASS
Navigating Cybersecurity Leadership Challenges with Insights from Pioneers
by Todd Fitzgerald
“CIS RAM is the first control standard to be applied to the new Duty of Care Risk Analysis Standard (DoCRA). It will be interesting to see how the acceptance of DoCRA progresses and the achieved level of adoption between the legal and security communities as it directly marries the risk assessment techniques noted in the Risk Management chapter, the legal practices noted in the security incident and it’s the law chapters, and this chapter on the security controls frameworks. There are clearly benefits of morphing to a more seamless conversation between the cybersecurity, legal, and business communities.”
Cybersecurity: Ethics, Legal, Risks, and Policies
By Ishaani Priyadarshini, Chase Cotton
“Another challenging aspect of cyber insurance and risk management is determining the acceptable risk for each organization. A ‘duty of care’ approach may be essential for protecting all interested parties like judges, regulators, executives, and the public who can be influenced by those risks. The duty of care risk analysis standard (DoCRA) lists principles and practices for balancing security, business objectives, and compliance, while developing security controls.”
Cyber Risk Management
Prioritize Threats, Identify Vulnerabilities and Apply Controls
By Christopher J Hodson
“CIS RAM focuses on the concepts of due care and appropriateness, via a ‘Duty of Care Risk Analysis’ (DoCRA) model.”
“The CIS RAM interoperates well with established risk frameworks such as ISO 27005 and NIST 800-30 and provides a set of control recommendations to evidence due care and appropriateness through templates, exercises and practical examples. CIS RAM also assists the organization in the creation of a risk register, something which can be overlooked.”
“CIS RAM’s principles and practices align to law, regulations and security standards. They are based on three overarching principles which are pragmatic and should be considered in any adoption of a risk management framework (Center for Internet Security, 2018):
- Risk analysis must consider the interests of all parties that may be harmed by the risk.
- Risks must be reduced to a level that authorities and potentially affected parties would find appropriate.
- Safeguards must not be more burdensome that the risks they protect against.”
Creating an Information Security Program from Scratch
By Walter Williams
“The Center for Internet Security developed CIS RAM based on their Critical Security Controls standard; however, it conforms to the standards established by ISO 27005, NIST SP 800-30, and RISK IT so that an organization looking to implement the critical security controls could have a standards-based means to determine what of the sub controls of the standard they would implement, and which would be deemed not acceptable.
CIS RAM is also based on the notion of Duty of Care Risk Analysis (DoCRA). This is an independent standard (https://docra.org) which represents principles and practices for analyzing risks that addresses the interests of all impacted parties.”
The Center for Internet Security, Inc. (CIS®)
Cybersecurity Where You Are Podcast: Conceptualizing Reasonableness for Risk Analysis
In episode 29 of Cybersecurity Where You Are, co-hosts Tony Sager and Sean Atkinson are joined by Chris Cronin, ISO 27001 Auditor and Partner at HALOCK, a leading information security consultancy and Board Chair of The DoCRA Council. Their discussion focuses on “reasonableness” as it relates to cybersecurity risk management. This topic isn’t just about proving to regulators, litigators, and others that security controls were in place prior to an incident. It also considers how to implement safeguards without overburdening users and executives.
RIMS RiskWorld 2022
The Questions a Judge Will Ask You After a Data Breach
In post-data breach litigation, you must demonstrate due care and reasonable control. Learn what basic questions the court will ask and how the duty of care risk assessment (DoCRA)—based on judicial balancing tests and regulatory definitions of reasonable risk—helps you answer them. Distinguish the risk assessment criteria that allow for comparison, reflect your organization’s values and hold up to public scrutiny. See how you can employ DoCRA to fulfill regulators’ requirements for a complete and thorough risk assessment following a data breach, with a valuable perspective for cyber insurance. Understand how to define ‘reasonable security’ through examples from ‘whistleblower’ movies and their risk management process.
PRESENTER: Chris Cronin, ISO 27001 Auditor | Board Chair – The DoCRA Council | Partner – HALOCK Security Labs
The Center for Internet Security, Inc. (CIS®)
CIS Risk Assessment Method (RAM) v2.1
CIS RAM (Center for Internet Security Risk Assessment Method) is an information security risk assessment method that helps organizations implement and assess their security posture against the CIS Critical Security Controls (CIS Controls) cybersecurity best practices.
This download will have a family of documents available as they are released.
Available Now:
- CIS RAM Core v2.1
- CIS RAM for Implementation Group 1 (IG1) v2.1 and Companion Workbook
- CIS RAM for Implementation Group 2 (IG2) v2.1 and Companion Workbook
Coming Soon:
- CIS RAM for Implementation Group 3 (IG3) v2.1 & Companion Workbook
Read the article on the CIS website
The Center for Internet Security, Inc. (CIS®)
CIS Risk Assessment Method (RAM) v2.0 for CIS Controls v8
The Center for Internet Security (CIS) recently released the CIS Risk Assessment Method (RAM) v2.0, an information security risk assessment method to help enterprises justify investments for reasonable implementation of the CIS Critical Security Controls (CIS Controls). CIS RAM helps enterprises define their acceptable level of risk, and then manage that risk after implementation of the Controls. Few enterprises can apply all Controls to all environments and information assets. Some Controls offer effective security, but at the cost of necessary efficiency, collaboration, utility, productivity, or available funds and resources.
CIS RAM was developed by HALOCK Security Labs in partnership with CIS. HALOCK has used CIS RAM’s methods for several years with positive response from legal authorities, regulators, attorneys, business executives, and technical leaders. HALOCK and CIS collaborated to bring the methods to the public as CIS RAM v1.0 in 2018, and now v2.0 in 2021. CIS is a founding member of the non-profit DoCRA Council that maintains the risk analysis standard that CIS RAM is built upon.
Read the article on the CIS website
LAW.COM
Sedona Conference Just Leveled the Playing Field with Reasonable Security
The Sedona Conference Working Group 11 (WG11) has provided the definition for reasonable security. In February 2021, The Sedona Conference released its Commentary on a Reasonable Security Test to help the regulatory and litigation communities “move the law forward in a reasoned and just way.” We now have a test for reasonable security practices that brings together the traditions of regulators, litigators, and information security communities to balance burdens of safeguards against the risk of harm to ourselves and others.
UPDATE ON REASONABLE SECURITY
Half of Your Cybersecurity Adversaries Just Disappeared
The Sedona Conference – an influential think tank that advices attorneys, regulators, and judges on challenging technical matters – just released its Commentary on a Reasonable Security Test. The Commentary is the first document of its kind that provides the legal community with a clear definition of a “reasonable” security control.
TECHOPEDIA
5 Cybersecurity Predictions for 2021
Measuring Reasonable Security
NATIONAL LAW REVIEW
Reasonable Security Practices Test: Sedona Conference Paper
Finding a Test for Reasonable Security Practices: Embrace Complexity and Specifics
“A working group of the Sedona Conference has proposed a solid answer to these questions. By its own description, the Sedona Conference is a nonpartisan, nonprofit research and educational institute dedicated to the advanced study of specific law and policy, including privacy and data security law. The Conference has just published a set of commentary on a reasonable security test. The paper is worth reading.”
NetDiligence® CYBER RISK SUMMIT
What is Reasonable Cyber Security
The panel provided an overview of the risk-based analysis process that substantiates the method, and presented the legal, regulatory, and security best-practice history that informs the method. Each participant presented why the method successfully substantiates the term “reasonable” in their work and provided anecdotes that illustrate how it has been used on their experience. The panel described a practical method that organizations can use for defining how the term “reasonable” applies to them, all attendees received an immediately applicable, and tangible benefit from the session.
DoCRA Council Board Chair, Chris Cronin, participated in the panel discussing reasonable security. The webinar provides a full perspective from legal, security, insurance, and regulatory views. The recording is now available at the NetDiligence website.
TOPICS:
- Terms and Definitions
- Various Standards of Reasonableness and Duty of Care
- Risk-Based Analysis and Best Practices
- Communicating to and Working with the Policyholder.
PANELISTS:
- Andrew Maher (M), AXIS
- Chris Cronin, HALOCK Security Labs
- Doug Meal, Orrick LLP
- Timothy Murphy, Office of Attorney General for the Commonwealth of Pennsylvania
A few key Q&As from the webinar:
Are there any risk frameworks which quantify risk in the way you’re describing?
CIS RAM by Center for Internet Security provides explicit instructions for how to do risk analysis to demonstrate balance and reasonableness. ISO 27005, NIST 800-30 imply or state that risk analysis should consider risk to self, interested parties, and mission (what courts may think of as “utility”).
Various carriers offer complementary risk engineering services, but insured’s rarely use the opportunity. If carrier’ make their terms subject to, there is push back saying that other markets are not requiring it. Do you think that carriers as a whole should push harder on requiring risk engineering to be completed?
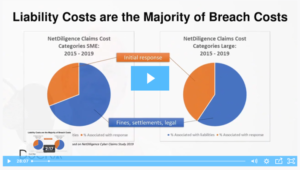
Yes! As an information security practitioner I see regulators and customers respond very well when they see a focused effort on risk reduction over time. The NetDiligence report shows the majority of claims payouts going to liabilities. One of the things I love about insurance is that when it manages risk, everyone wins.
Does PA recognize CIS controls for assessment ?
Yes, PA listed CIS controls by name in a recent settlement along with other industry-appropriate control standards such as NIST and ISO 27001.
Are there cases I can review to better understand Reasonable security?
Pennsylvania’s settlement with Orbitz and Expedia, https://www.attorneygeneral.gov/wp-content/uploads/2019/12/19-12-12-Orbitz-AVC-EFILING.pdf
I am in Medical Technology Cybersecurity. We follow NIST and CIS Controls within the hospitals risk appetite and budget. Less funds available due to Covid19 and reduced revenue.
It would be highly questionable whether “less funds available” would be considered a valid reason for not employing data security measure that would otherwise be considered “reasonable” under industry standards, applicable statutes/regulations, or cost-benefit analysis.
Additionally from Chris:
If you use CIS Controls, then also look at CIS RAM the risk assessment method. They show you how to do this risk analysis.
View the recording.
NATIONAL LAW REVIEW
HIPAA Risk Analysis 2.0: Duty of Care Risk Analysis [PODCAST]
In this episode, Foley Partner Jen Rathburn sits down with Terry Kurzynski, found of HALOCK Security Labs on the Duty of Care Risk Analysis, especially as it pertains to health care.
DARK READING
Defining “Reasonable” Security at (ISC)2 Security Congress
Approaching Reasonable Security for Regulatory Requirements such as The SHIELD Act, CCPA, California’s Internet of Things (IoT) and more
DARK READING
How to Create Smarter Risk Assessments
Executives and directors need quantitative measurements – such as likelihood of loss and hard-dollar financial impact – to make more informed decisions about security risks. (CIS RAM)
SECURITY MAGAZINE
Who in an organization is responsible for a data breach?
CIS® (Center for Internet Security, Inc.)
CIS is a founding member of the DoCRA Council that maintains the risk analysis standard that CIS RAM is built upon. CIS RAM FAQs
MIDWEST CYBER SECURITY ALLIANCE
Presentation on Duty of Care Risk Analysis: Leveraging the New Risk Assessment Method to Reduce Liability
https://www.midwestcyber.org/september-2018-meeting/